Example 1: Maintain User Accounts Externally using LDAP
This example demonstrates how you might configure Geo SCADA Expert so that its User accounts are integrated with LDAP user accounts. With such a configuration setup, IT staff are able to maintain the Geo SCADA Expert User accounts externally, rather than by having to log on to Geo SCADA Expert.
Although this example demonstrates some settings that are specific to LDAP integration, the overall concept could equally apply to integrating Geo SCADA Expert User accounts with Windows domain user accounts and user groups.
With this example, users are able to log on to Geo SCADA Expert using their more familiar LDAP user names, rather than the user names that have been configured for their Geo SCADA Expert User accounts. Additionally, the Geo SCADA Expert User Groups are integrated with the LDAP user groups, so that the IT staff are able to maintain user group membership externally, outside of Geo SCADA Expert. Where possible, Geo SCADA Expert security permissions have been assigned to the User Groups, rather than the individual User accounts, to enable access to those permissions to be updated in conjunction with the User Group membership updates.
The IT staff at a particular company use LDAP to maintain user credentials and other security-related information centrally across the company intranet. They want to integrate Geo SCADA Expert's User accounts with LDAP so that they can continue to maintain the user accounts centrally, without having to access Geo SCADA Expert to maintain the user accounts once the initial setup is complete. Additionally, they would like users to be able to log on to Geo SCADA Expert using their LDAP user names with which they are already familiar, rather than the less familiar Geo SCADA Expert user names. Some of the existing LDAP user names do not adhere to Geo SCADA Expert's naming convention, so they would particularly like to retain the ability for users to log in to Geo SCADA Expert using such user names.
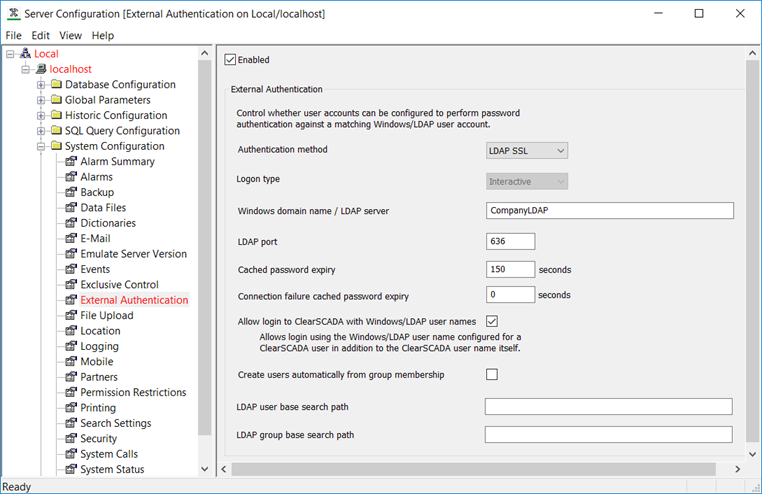
An administrator sets up the External Authentication requirements on the server, using the Geo SCADA Expert Server Configuration tool. The settings specify that the company will be using the more secure LDAP SSL method to authenticate logon credentials against LDAP user accounts stored on the LDAP server 'CompanyLDAP'. Additionally, the check box for 'Allow login to Geo SCADA Expert with Windows/LDAP user names' is selected, to enable users to use their more familiar LDAP user names for logging in to Geo SCADA Expert.
The administrator then logs on to ViewX to set up the required Geo SCADA Expert User accounts - one for each LDAP user that requires operator- or engineer-level access to Geo SCADA Expert. As the company has opted not to create users automatically from group membership, they have also opted to integrate their administrator-level Geo SCADA Expert User accounts with LDAP. (If they had opted to create users automatically from group membership, they would have opted not to integrate their administrator-level Geo SCADA Expert User accounts with LDAP. To facilitate this, they would have used separate Geo SCADA Expert User Groups to which they could assign administrator-level security permissions, but would not have linked those User Groups to external LDAP user groups. This would help to prevent the automatic creation of new user accounts with high-level security permissions, such as those that allow the Geo SCADA Expert server to be shut down.)
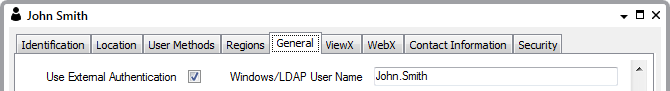
Each User account is configured to Use External Authentication and is associated with a corresponding LDAP user account:
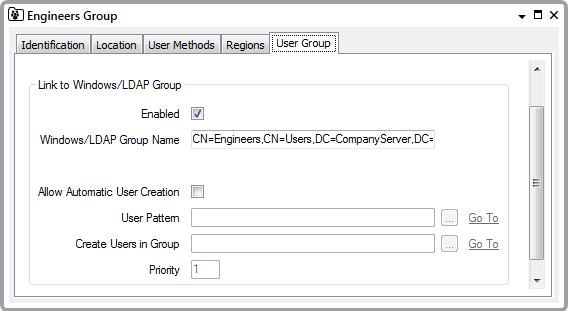
Each Geo SCADA Expert User Group that is to be associated with an LDAP user group is configured with the name of the relevant LDAP group. Care is taken to ensure that the full DN (Distinguished Name) of the LDAP group is specified.
The company does not want Geo SCADA Expert to create User accounts automatically if someone attempts to log on with an LDAP user name for which no User account exists in the database. As such, the 'Allow Automatic User Creation' check box is left clear on each User Group Form.
The administrator uses the Database Bar to access the Security window of the relevant 'object' Groups and/or individual items in the database. They use the Security window to assign the required access and security permissions to those Groups or items from the User Groups. Users that are members of those User Groups automatically inherit the same access and security permissions for those Groups and items in the database.
With the above configuration, users are able to log on to Geo SCADA Expert using their LDAP user names. Additionally, IT staff are able to update the users' User Group membership externally in LDAP. When a user logs on to Geo SCADA Expert, their User Group membership is checked and updated in line with the LDAP user groups for which corresponding User Groups exist in the Geo SCADA Expert database. The entries in the User Groups field on the relevant User Form update automatically in line with the changes in User Group membership.
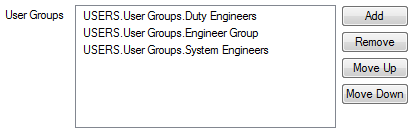
As many of the security permissions have been assigned to the User Groups, rather than the individual User accounts, the permissions to which a user is assigned update automatically at logon, in line with any changes in User Group membership.
Further Information
Enable External Authentication: see Using External Authentication with Geo SCADA Expert.
Allow Login to Geo SCADA Expert with Windows/LDAP User Names: see Using External Authentication with Geo SCADA Expert.
External Authentication properties on User Forms: see Define whether a User is Associated with a Windows or LDAP User Profile.
Associate a Geo SCADA Expert User Group with a Windows Domain Group or LDAP User Group.
Assigning Security Permissions: see Working with the Security Window.