Server Operating System Manual Hardening
The following are features that you can manually configure to provide additional security for the server operating system:
To reduce attack surfaces, Network communication protocols should be limited to only those which are required.
We recommend that the following items should be disabled from each local network interface installed on the machine. You should check that they are not used or required as part of the customer architecture.
- QOS Packet Scheduler
- Internet Protocol 6 (TCP/IPv6)
You should consider disabling the local admin shares as a possible security measure. However, this will be dependent upon any additional software which may use the admin shares for data transfer, or if there are future requirements to deploy software remotely.
Microsoft does not recommend this change and therefore careful consideration must be taken into account if you wish to lock down the admin shares.
To disable the admin shares, you can apply the following registry key setting:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
"AutoShareWks"=dword:00000000
We suggest this is only performed once all the required software installations, especially AV deployments have been completed as they often require the use of the ADMIN$ share for file transfer.
To enable admin shares, apply the following value:
"AutoShareWks"=dword:00000001
For Original WebX, it is recommended to change the SSL Cipher list to remove any old or known security risk ciphers (such as anything which is MD5 based).
Access the application registry at:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Schneider Electric\ClearSCADA\Server
Apply the settings shown below. This removes any MD5 based ciphers from the available list. MD5 is now considered vulnerable.
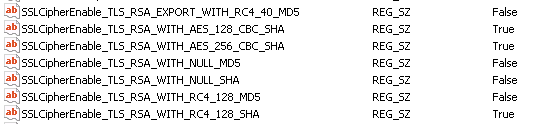
Many (older) browsers require RC4_128_SHA to connect as they do not all support AES.
When Terminal Services are used, ensure that the property 'Allow connections only from computers with NLA' is set.