Configure the Connection Security Settings
You use the Connection Security section of the Geo SCADA Expert Server Configuration Tool to set up the server's certificate settings for communications with the other servers and clients on your system. The Connection Security section is located within the System Configuration branch of the tool. We strongly recommend that you set up your system to use trusted certificates to initiate secure connections and encrypt the data that is transmitted between the Geo SCADA Expert servers and clients. For more information about the use of certificates and also about the configuration settings that are required for client certificates, see Certificates for Geo SCADA Expert Server and Client Connections.
You use the Connection Security section of the Geo SCADA Expert Server Configuration Tool to configure these settings:
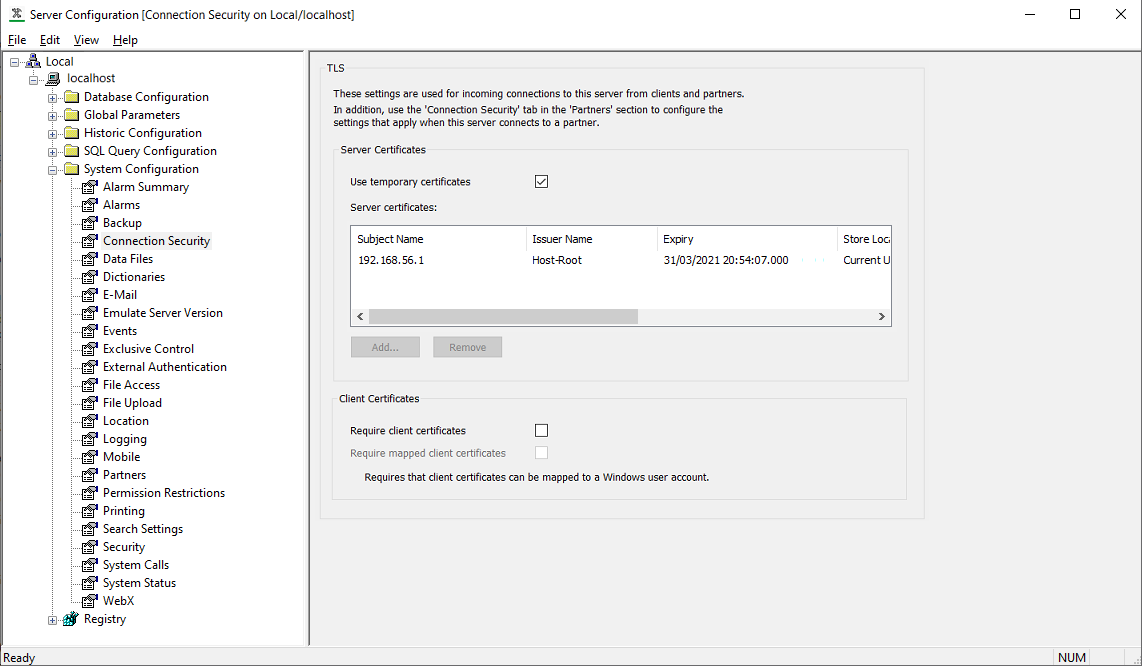
Server Certificates
You use the properties in this section to specify whether the server uses certificates for communications with other servers and clients, and if so, which certificates are used.
On systems on which server certificates are used, the Geo SCADA Expert server provides its certificate to the clients, so that the clients can verify that the server is a valid Geo SCADA Expert server. The client will decline the connection if the server does not have a valid certificate (or has no certificate at all) (see Certificates for Geo SCADA Expert Server and Client Connections). The exception to this is clients that are running a version of Geo SCADA Expert that is earlier than Geo SCADA Expert 2020. Such clients use a different communications protocol and are exempt from requesting valid server certificates.
- Use Temporary Certificates—Select this check box for the server to use a self-signed certificate (rather than a certificate obtained from a trusted certification authority). The self-signed certificate is generated on server start-up. You might choose this option, for example, while waiting to receive the trusted certificates, after which you should update the configuration in this section of the tool.
If this check box is selected, ensure that each client connection is configured to have its Validate Server Certificate check box clear (see Configure the Client Connection Security Settings in the Geo SCADA ExpertGuide to Client Administration).
Clear the Use Temporary Certificates check box when the server uses certificates that have been obtained from a trusted certification authority (in which case, you need to populate the Server Certificates field accordingly).
- Server Certificates—Use this field to list the trusted certificates that the server is to use for communications with other servers and clients. Each certificate must have a private key associated with it. Obtain the certificates from a trusted certification authority, and then load them into the server machine's Windows certificate store. For more information about certificate stores, see the Windows help.
To add the certificates to the Server Certificates list, use the Add button (see Add a Certificate to the Server Certificates List).
To remove an obsolete certificate from the list, select the obsolete certificate, followed by the Remove button.
inability to synchronize databases and take over as main
If a Standby server is unable to connect to the Main server due to a TLS configuration conflict, the Server Icon on the Standby server will go magenta to indicate that an issue has been detected. The Server icon's context-sensitive menu will indicate that there is Invalid Standby Configuration and the dialog box will provide further information about the issue (see The Server Icon). If this is due to a TLS configuration conflict, you should check both sets of Connection Security settings on both servers and ensure that there are no issues with the certificates that either server is using. For example, a conflict will occur if the Standby server is configured to validate partner certificates, but is not able to do so because the Main server is using a temporary certificate. Do not perform any manual changeovers until the TLS configuration conflict has been resolved.
If the Main server goes offline before the Standby server has been able to complete the synchronization process, that Standby server will not be able to take over as Main. If no other Standby servers exist or have fully synchronized databases and a changeover occurs, this could result in the system going offline. To bring the system back online, restart the server that was Main. If that is not possible, contact Schneider Electric for assistance. You might be advised to restore the database on one of the servers that has an invalid database, using the most up-to-date backup in order to minimize data loss. Following this, ensure that all of the servers have compatible Connection Security configuration to enable successful synchronization to occur, and that any other issues that might be preventing synchronization have been resolved (see Check that Standby Servers are Synchronized with the Main Server).
Client Certificates
You use the properties in this section to specify whether the server is only to communicate with clients that provide valid client certificates, and if so, to specify various settings for those certificates. (If client certificates are used, you also need to set up the required client connection security for each client (see Configure the Client Connection Security Settings in the Geo SCADA ExpertGuide to Client Administration).)
On systems on which client certificates are used, each client is required to provide a valid certificate to the server, so that the server can verify that the client is a valid client. The connection request is declined if the client does not have a valid certificate (or has no certificate at all) (see Certificates for Geo SCADA Expert Server and Client Connections). The exception to this is clients that are running a version of Geo SCADA Expert that is earlier than Geo SCADA Expert 2020. Such clients use a different communications protocol and are exempt from requiring valid client certificates.
- Require Client Certificates—Select this check box for clients that are running Geo SCADA Expert 2020 onwards to provide a valid client certificate to the server.
Clients that are running a version of Geo SCADA Expert that is earlier than Geo SCADA Expert 2020 are exempt from requiring valid client certificates and can still communicate with a server that has been updated to require client certificates.
Clear the check box (not recommended) if the server is not to request a valid client certificate from each client.
- Require Mapped Client Certificates—Select this check box if the Geo SCADA Expert server is only to accept client certificates that map to a Windows user account. For more information about providing this mapping, see the Windows help.
Clear the check box if the server does not require the client certificates to be mapped to a Windows user account.
potential security breach
Apply the changes to the server.
The changes take effect immediately.
Remember to make similar configuration changes to any other servers in your system.
Further Information
Understand the information that is displayed in the Server Certificates field: see Add a Certificate to the Server Certificates List.
Configure the Connection Security settings that apply to outgoing server-to-server connections when this server connects to another server as a client: see Connection Security Tab (for Server-to-Server Communications).