You can configure your system so that Virtual ViewX and Original WebX clients can access the Geo SCADA Expert database via non-secure HTTP connections (see Define the Listen Port Settings for Original WebX Clients). As HTTP connections are unsecure, potentially the communications could be intercepted and used for malicious purposes. For this reason, Geo SCADA Expert has certain safeguards in place by default:
- If you have HTTP (unsecure) and HTTPS (secure) ports enabled, Geo SCADA Expert will automatically use HTTPS for logging on and writing to the database (issuing controls, and so on.). The HTTPS port is used even if the Virtual ViewX or Original WebX user initially connected via a HTTP port. When HTTPS is available, Geo SCADA Expert uses it in preference to HTTP to help protect your system from unauthorized access.
- If you have HTTP ports enabled, but HTTPS ports disabled, Geo SCADA Expert will only allow users to browse by default. They will not be able to log on or issue controls.
- ViewX scripts use an alternative connection to the server. This connection automatically uses HTTP or HTTPS depending on the selected configuration, defaulting to HTTPS if both are available. You can specify the certificate validation that is done by ViewX on the server certificate when using HTTPS.
However, in certain specific circumstances (such as testing a system), there may be a need for an engineer to log on and issue controls via an unsecure connection. To facilitate this, the Server Configuration Tool’s WebX settings include the following settings:
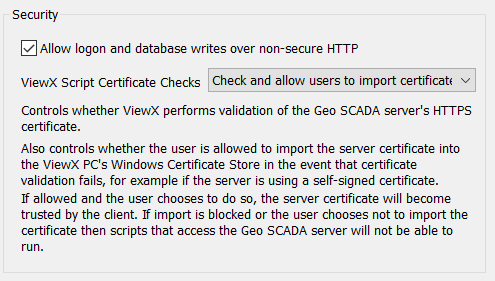
- Allow Logon and Database Writes Over Non-Secure HTTP—Select this check box to enable engineers to log on and issue controls over an HTTP connection. The setting also accommodates requests that are forwarded by a proxy.
You should only select this check box if you are fully aware of the security risks and are prepared to accept the lowered level of security. We do not advise selecting the check box on a fully commissioned live system. Once the commissioning work using non-secure connections is complete, and before the system goes live, ensure that the check box is cleared so that log ons and write actions only take place over secure connections.
NOTICEPOTENTIAL SECURITY BREACH
Do not select the Allow Logon and Database Writes Over Non-Secure HTTP check box unless you are fully aware of the security risks and are prepared to accept the lowered level of security. We do not advise selecting the check box on a fully commissioned live system. The Allow Logon and Database Writes Over Non-Secure HTTP check box should be clear so that log ons and write actions to the database only take place over secure connections.Failure to follow these instructions can result in equipment damage. - ViewX Script Certificate Checks—Use to select the level of script certificate checks required. Also use to control whether users are allowed to import the server certificate into the ViewX PC's Windows Certificate Store in the event that certificate validation fails, for example if the server is using a self-signed certificate. Choose from:
- None—Select this option if you do not want users to run any ViewX script certificate checks. This is the default setting for Geo SCADA Expert 2020.
- Check and allow users to import certificate—Select this option to run a check and allow users to import a certificate.
With this option selected, if the existing certificate is not valid when a script runs, the Windows Certificate Check dialog box is displayed. The dialog box allows the user to view and add the server certificate to the client machine. If the user chooses to import the certificate, the server certificate will become trusted by the client and the dialog box should no longer appear when running a script. This is the default setting for Geo SCADA Expert 2021 onwards.
- Check and block import of certificate—Select this option to run a check and prevent users from importing a certificate.
With this option selected, if a valid certificate is not already loaded on the client machine then scripts that access the server will not be able to run. When a user attempts to make an HTTPS connection through a script, a pop-up window is displayed to inform the user that no valid certificate is available and they cannot import one through ViewX. To prevent this, you have to add the server certificate to the client machine. You have to do this outside of ViewX and Virtual ViewX, using the client machine's built-in tools. The built-in tool for Windows® is the Certificate Manager application, which is accessible via the Start menu, Control Panel, or command prompt.
These certificate checks only apply to HTTPS connections between ViewX and Virtual ViewX machines and the Geo SCADA Expert server. If the Virtual ViewX server is on the same machine as the Geo SCADA Expert server, the Virtual ViewX server does not have to run the checks, even if any of the ViewX Script Certificate Checks options are selected. Certificate checks do not apply to HTTP connections.