Connection Security Tab (for Server-to-Server Communications)
The Partners section of the Server Configuration Tool includes a Connection Security tab. Use the tab to specify the security settings that apply to outgoing server-to-server connections. The settings on the tab apply when the Geo SCADA Expert server on which you are configuring the settings acts as a client that is connecting to another Geo SCADA Expert server. The other server with which this server communicates is known as the 'partner' server.
The Connection Security tab is only available for use on multi-server Geo SCADA Expert systems (whereby the server is set to a Type other than Lone Server (see Set the Type of Server)).
Use the Connection Security tab to configure these settings on the local Geo SCADA Expert server:
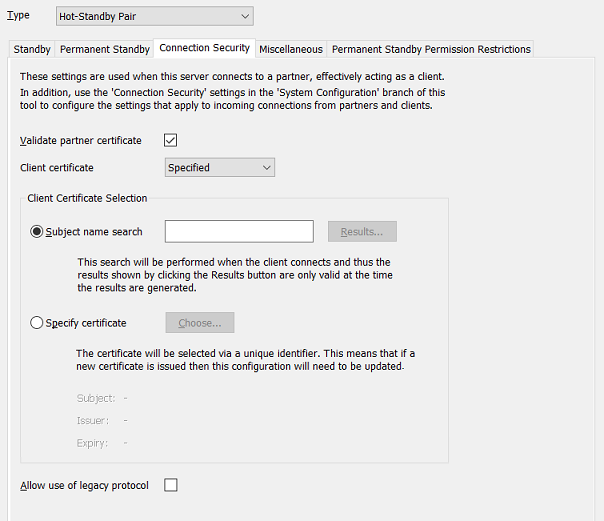
- Validate Partner Certificate—Select this check box if the other servers to which this server is to connect use certificates that have been obtained from a trusted certification authority.
Clear the check box if the other server machines use self-signed certificates. (If this is the case, the Use Temporary Certificates check box has to be selected in the Connection Security section within the System Configuration branch of the Server Configuration Tool on those other server machines (see Configure the Connection Security Settings).)
- Client Certificate Mode—Use this property to specify how certificates on this server are selected for providing to any of the partner servers that request a client certificate, when this server attempts to connect to those servers as a client. Chose from:
- Disabled—Not recommended. This server does not use client certificates for communications with other Geo SCADA Expert servers. Select this option if none of the other servers with which this server is to communicate are configured to Require Client Certificates (see Configure the Connection Security Settings).
The fields in the Client Certificate Selection section of the window will be 'grayed out' and unavailable for use.
- Automatic—Choose this option or the Specified option (see below) if any of the other servers with which this server is to communicate are configured to Require Client Certificates (see Configure the Connection Security Settings). If the partner server requests a certificate when communications are initiated, this server will provide one. The client certificate will be selected automatically, based on the CA root certificates that the partner server trusts. The fields in the Client Certificate Selection section of the window will be 'grayed out' and unavailable for use.
- Specified—Choose this option or the Automatic option (see above) if any of the partner servers with which this server is to communicate are configured to Require Client Certificates (see Configure the Connection Security Settings). If the partner server requests a certificate when communications are initiated, this local server will provide one. Select this option if you want to specify the certificate that this server uses for communications with other Geo SCADA Expert servers. Use the fields within the Client Certificate Selection section of the window to do this.
- Disabled—Not recommended. This server does not use client certificates for communications with other Geo SCADA Expert servers. Select this option if none of the other servers with which this server is to communicate are configured to Require Client Certificates (see Configure the Connection Security Settings).
- If the Client Certificate Mode is set to 'Specified', use the fields in the Client Certificate Selection section of the window to specify one of the following:
- Subject Name Search—Use to restrict the available client certificates to just those that meet the search criteria specified in this field. This field is a 'contains' field, so the search results (access via the Results button) list those valid certificates that contain the character or character combination that you specify in this field. For example, if you specify the letter a, it will display those certificates that include the letter a in their Subject Name field. Likewise, if you specify the text e.1, it will display those certificates that include that specific string in their Subject Name field.
When communications are initiated, if multiple valid certificates match the search string, they will be filtered based on the CA root certificates that the partner server trusts, after which a certificate will be selected arbitrarily.
Be aware that the actual search will be performed at the time that the client connection is initiated. As such, the client certificates that are available at that time might differ to those shown in the Results window when you are setting up the search criteria. For example, certificates that have expired will no longer meet the search criteria, while other newly added certificates might fulfill the search criteria.
- Specify Certificate—Use this option to specify a particular certificate.
If you choose this option, be aware that this configuration will need updating whenever a new certificate is issued.
Select the Choose button to display a window from which you can select the relevant certificate, from the certificates that are loaded into the local server machine's Windows certificate store. The following details are displayed about the chosen client certificate, in the Connection Security window:
- Subject—The entity with which the certificate's public key is associated.
- Issuer—Information that identifies the organization that issued the certificate.
- Expiry—The date and time at which the certificate will expire (shown in Local Time). It is important to renew certificates well in advance of their expiry time. (Remember to update the Specify Certificate configuration as soon as the certificate has been renewed.)
- Subject Name Search—Use to restrict the available client certificates to just those that meet the search criteria specified in this field. This field is a 'contains' field, so the search results (access via the Results button) list those valid certificates that contain the character or character combination that you specify in this field. For example, if you specify the letter a, it will display those certificates that include the letter a in their Subject Name field. Likewise, if you specify the text e.1, it will display those certificates that include that specific string in their Subject Name field.
- With the Allow use of legacy protocol check box either:
- Clear the check box (the default on new installations) for this server to only connect to partner Geo SCADA Expert servers that support the new more secure protocol (Geo SCADA Expert 2020 onwards).
- Select the check box (the default on upgrades from older system definitions) to enable this server to connect to all Geo SCADA Expert servers that are running a supported version of Geo SCADA Expert, regardless of protocol. The server will use the legacy protocol when connecting to partner servers that are running Geo SCADA Expert 2019 or earlier versions of software.
We recommend that you clear this check box once all of your servers have been upgraded to use the new more secure protocol.
inability to synchronize databases and take over as main
If a Standby server is unable to connect to the Main server due to a TLS configuration conflict, the Server Icon on the Standby server will go magenta to indicate that an issue has been detected. The Server icon's context-sensitive menu will indicate that there is Invalid Standby Configuration and the dialog box will provide further information about the issue (see The Server Icon). If this is due to a TLS configuration conflict, you should check both sets of Connection Security settings on both servers and ensure that there are no issues with the certificates that either server is using. For example, a conflict will occur if the Standby server is configured to validate partner certificates, but is not able to do so because the Main server is using a temporary certificate. Do not perform any manual changeovers until the TLS configuration conflict has been resolved.
If the Main server goes offline before the Standby server has been able to complete the synchronization process, that Standby server will not be able to take over as Main. If no other Standby servers exist or have fully synchronized databases and a changeover occurs, this could result in the system going offline. To bring the system back online, restart the server that was Main. If that is not possible, contact Schneider Electric for assistance. You might be advised to restore the database on one of the servers that has an invalid database, using the most up-to-date backup in order to minimize data loss. Following this, ensure that all of the servers have compatible Connection Security configuration to enable successful synchronization to occur, and that any other issues that might be preventing synchronization have been resolved (see Check that Standby Servers are Synchronized with the Main Server).
Further Information
Configure the Connection Security settings for when this server communicates with client machines: see Configure the Connection Security Settings.
Configure the Connection Security settings on client machines: see Configure the Client Connection Security Settings in the Geo SCADA Expert Guide to Client Administration.