When you have displayed the Security window for an item (see Accessing the Security Window for a Database Item), you can use the following settings to define the security features for the selected item:
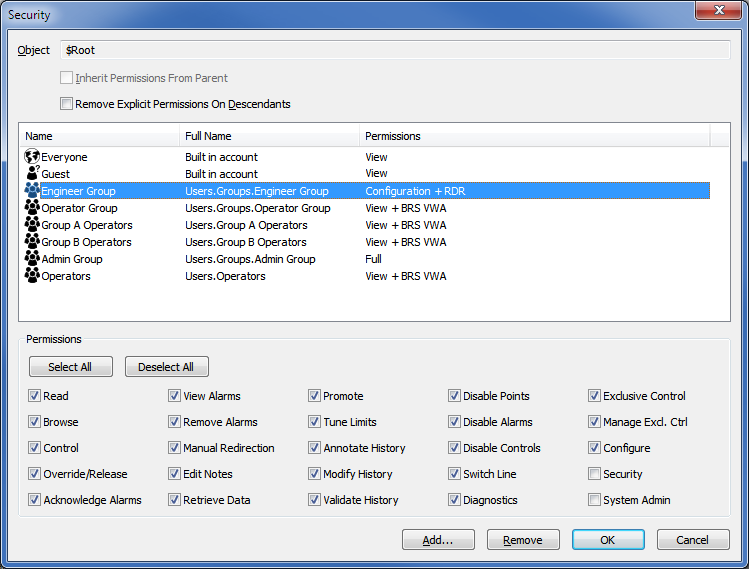
At the very top of the Security window, the name of the database item to which the security settings apply is displayed. For example, on the Root Group, the name is $Root (the system root).
This check box is selected by default on new database items. When selected, it means that the ACL for the database item is removed, forcing the database item to use the security permissions that are allocated to its parent Group (the Group that contains the item, which may be the System or Root group). If you want the database item to have its own security settings and not inherit those of the parent group, you need to clear this check box. Clearing the check box makes the permission check boxes at the bottom of the Security window become available for use. You can use the Permission check boxes to define the ACL for the database item.
This check box is only available on Group items and it allows you to specify whether the ACLs of the items in the Group are deleted and replaced with the same permissions that you configure for the Group.
If you select the check box, the items in the Group have their ACLs deleted which forces them to inherit the ACL of the Group.
If you clear the check box, the item's 'children' will retain their individual ACLs and may not inherit the security settings of the Group.
Below the Remove Explicit Permissions on Descendants check box is a display area that shows the user accounts and User Groups that have permissions to access the selected item. The display shows the
If you select one of the user accounts or User Groups, you will see that the Permissions check boxes at the bottom of the Security window change to show which permissions have been allocated to the account or User Group.
To reduce the time taken to manage user permissions, we recommend that you allocate security permissions to User Groups, rather than to individual User accounts. (The Users that are 'members' of a User Group inherit their security permissions from those User Group(s).)
This is particularly a requirement on systems that Integrate Geo SCADA Expert User Accounts with Active Directory or LDAP User Accounts. On such systems, Geo SCADA Expert automatically updates a user's User Group membership each time the user logs on. (This automatic update only applies to User Groups that are integrated with Windows domain groups or LDAP user groups.) As such, the security permissions that are assigned to the user get updated automatically in line with any changes in User Group membership.
Security threat
The Permissions check boxes show which of the database item's features are available for the selected User or User Group.
The availability of the permissions shown is dependent on the Permission Restrictions settings (see Define whether any Permissions are Restricted). By default, the Unacknowledge Alarms and Assign Alarm Responsibility permissions are restricted and so are not available.
The selected check boxes indicate the permissions that have been allocated; the blank check boxes indicate the permissions that the user account or User Group have not been allocated.
When you add a User or User Group in the Security Window the View, Browse
SECURITY THREAT
Each user account has the permissions for the 'Everyone' User Group, the User Groups of which the account is a member, and the permissions allocated to the user account itself. The only exception to this rule is the Guest user account which is not a member of the Everyone User Group.
These two buttons allow you to select or deselect all the permissions.
For more information on the individual permissions, see Permissions for Database Items.
Example:
A user account named 'Engineer1' is a member of a User Group named 'Engineers'.
The Root Group is configured to have the following security settings:
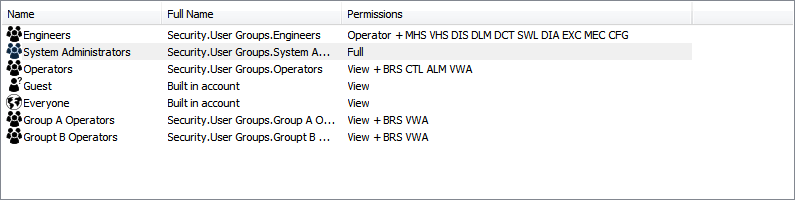
The Everyone User Group and Guest User account have the Read permission.
When you are allocating permissions, remember that the permissions that are allocated to the Guest user are available to anyone. Also, the permissions that you allocate to the
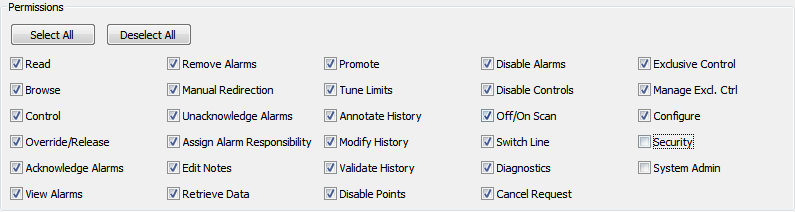
The System Administrators User Group is allocated Full permissions.
The Operators User Group is allocated the Read, Browse, Control, Acknowledge Alarms, and View Alarms permissions.
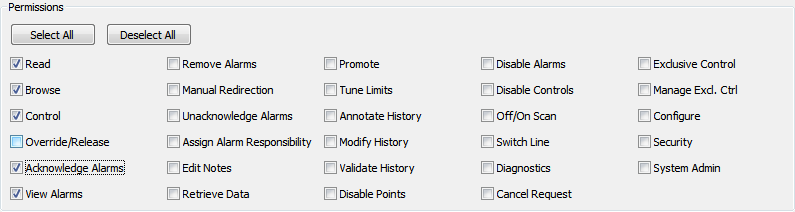
The Engineers User Group (to which the user account 'Engineer1' belongs) is allocated all permissions except Security and System Admin for the Root Group.
Use this button to display the Add Permissions window. You can use the Add Permissions window to add a user or User Group to the ACL. When a user account or User Group is shown on the Security window, you can allocate its permissions.
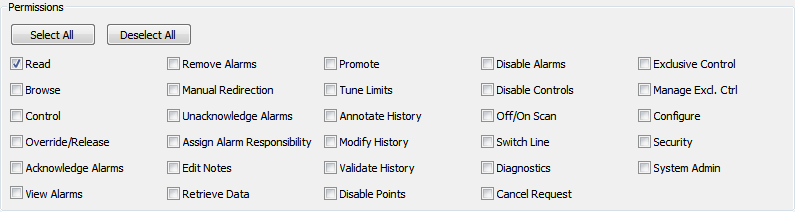
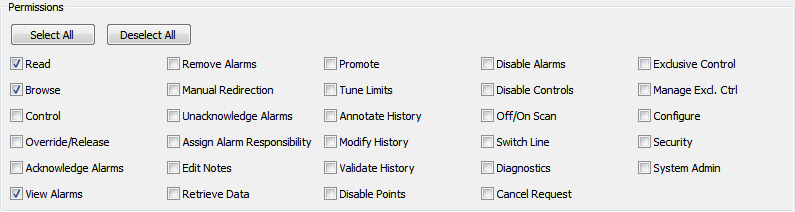
By default, when you add a new User Account or User Group to the ACL the permission settings are Read, Browse and View Alarms, equivalent to a Guest operator, as shown below.
Use to remove a user account from the ACL. When you remove a user or User Group from the ACL, that user or User Group will not have access to the selected item (unless it is a member of a User Group that remains in the list).
Further Information